Make your Pcap files GDPR and NISTIR 8053 compliant today!
Pcap files often contain personal data of network users, information about networks internal structure and other sensitive data. GDPR and NISTIR 8053 privacy rules make it difficult to share Pcap files with suppliers, customers, and even internally.
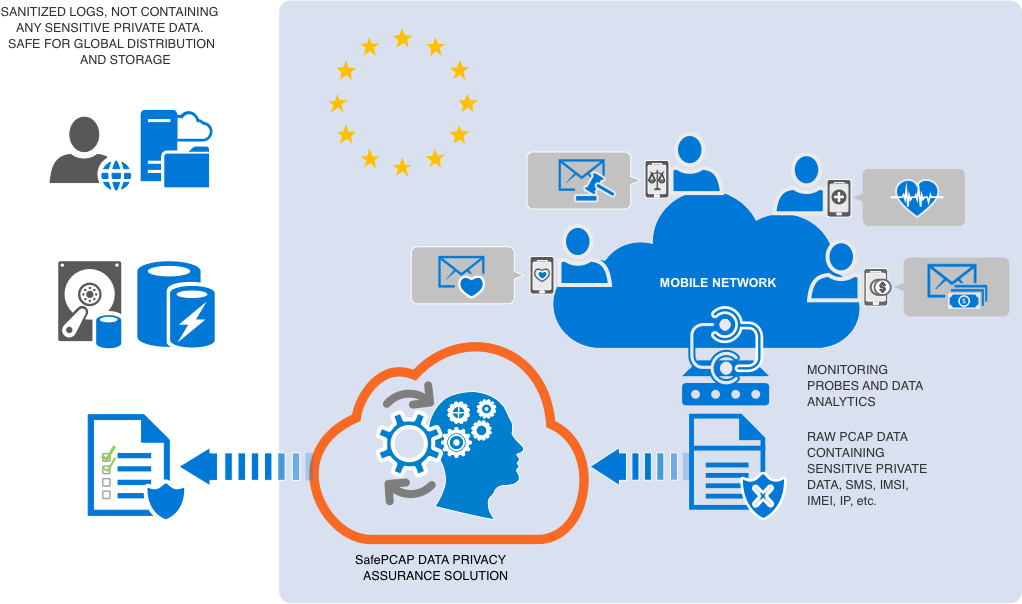 |
SafePcap allows automated scrambling of Pcap data in situ for any network stack at any stack layer while fully preserving the binary integrity of the data. Data modifications are done in a break-proof manner with the lengths, checksums, offsets and all other service fields recalculated on-the-fly for all affected packets and protocol layers.
Many network protocols/stacks are supported. Support for any new network protocol could be added quickly.
A file processed with SafePcap allows for effective forensic analysis with commonly used Pcap analysis tools such as Wireshark™.
Pre-programmed anonymization algorithms. Auto scrambling of IP addresses at all layers, phone and IMSI numbers, texts, email addresses, etc.
NISTIR 8053 specified reversible anonymization algorithms are supported.
Flexible and mature architecture allows easy customisation per individual customer reqs.
SafePcap is a scriptable L2-L7 Pcap anonymizer, sanitizer, scrambler, and a GDPR/NISTIR 8053 Compliance Solution. A file sanitized with SafePcap allows for effective forensic analysis with commonly used Pcap analysis tools like Wireshark™. Automation is fully supported via SafePcap CLI and the API.
Yes
Full support for all 5G/4G/LTE 3GPP Mobile Core protocols and interfaces including SS7, RANAP, DIAMETER, VoLTE, HTTP/2, etc.
Other tools can't anonymize binary encoded stack layers above TCP/UDP/SCTP. Instead, they take a simplistic approach of zeroing them out. This approach makes effective analysis of anonymized 3GPP Mobile Core Pcap files impossible.
A good analysis of the difficulty involved was posted in 2017 here. Our response is here. SafePcap by design allows anonymization of any field at any stack layer above TCP/UDP/SCTP without breaking packets' binary integrity.
IP Addresses, port numbers, IMSI and MSISDN numbers, texts, email addresses, passwords, domain names, etc. While not PII, MCC/MNC are considered sensitive by some. In fact, data at any stack layer could be considered sensitive in some use case. SafePcap allows targeted anonymization of captured network traffic at any stack layer while fully preserving the packets' binary integrity. Specific values in specific data fields at specific network layers could be easily targeted for bulk anonymization.
A Packet Capture (Pcap) file holds "bits on the wire" networking data, a time-stamped collection of captured network packet binaries. While sharing of Pcap files is essential for development, monitoring, and troubleshooting of computer networks, the PII (Personally Identifiable Information) and other sensitive info often found there makes sharing Pcap files "as is" problematic. The files have to be sanitized first.
Selectively anonymizing/scrambling/sanitizing PII and other sensitive info in captured network traffic while fully preserving the binary integrity of the data is a complex task due to a variety of protocols involved and the intricacy of packets' intra- and inter-dependencies.
Historically the Pcap sharing problem has been addressed by having NDAs between the parties involved.
Without the NDA the most popular approach is to dump the decoded frames into text format, obfuscate the sensitive data there, then share the results. Yet another approach is to zero out the packet data above TCP/UDP/SCTP. In both cases the resulting loss of information often makes network troubleshooting impossible.
GDPR and NISTIR 8053 make sharing of Pcap files even more problematic. PII can no longer be sent outside the EU even within the same entity.
SafePcap was built from the ground up to address this problem.
Any protocol one can decode/dissect with WireEdit today can be anonymized with SafePcap today.
Ubuntu 16.04/18.04/20.04, RHEL 7/8, CentOS 7/8.
Yes. This is similar to wiping out a patient name from a medical record, no matter what the name is. We can target for anonymization any packet field at any stack layer by the field name only. The field value will be replaced by dummy data or pseudonymized according to user preferences. The integrity of the anonymized packets and the anonymized Pcap file as a whole remains intact. The file can be analyzed with Wireshark™ as usual.
If SafePcap doesn't support the protocol involved, or the issue is in a specific field of a supported protocol, just telling us may be enough. As the last resort we may ask for a Pcap example file with at least one packet. You can anonymize the packet manually with WireEdit and share the anonymized copy.
Yes. All stacks, all layers, any encoding, binary and text based. If a layer is encrypted, the decryption keys can be extracted from the captured traffic and the algorithm allows for encryption of the anonymized data, we can support it. All the stack layers dissected by Wireshark™ before anonymization are dissected after without errors. Packets' binary integrity is fully preserved. Support for a new network stack can be added quickly. Having specs helps.
Yes. We support format preserving encryption of sensitive data at all stack layers. A customer holds a secret key which makes the pseudonymization reversible.
No.
C++.
Yes.